This blog was originally published by Cerby here.

Zero Trust has become one of the cybersecurity world’s most misunderstood buzzwords. In theory, it’s simple: never trust, always verify. In practice, it’s often reduced to a check-the-box product deployment or a single vendor’s promise to “solve” it for you.
But Zero Trust is not something you can buy, deploy, and move on from. Zero Trust is a journey, not a project.
Zero Trust is a security strategy. It is a model that requires organizations to rethink how they define trust, enforce controls, and manage danger. It’s not a silver bullet. It’s a discipline. And when it’s done right, it reshapes how security teams operate—from the ground up.
After working with countless organizations and watching Zero Trust go from concept to global adoption, here are four truths security leaders often miss—and what they should be doing instead.
1. Zero Trust security starts with visibility, not assumptions
Every Zero Trust security strategy should begin with a simple but often overlooked question: what exactly are we protecting?
It’s tempting to assume you already know, especially if you’ve invested in centralized identity tools like Identity and Access Management (IAM) and Identity Governance and Administration (IGA). But enforcing access doesn’t mean you have the full picture. These tools only see the applications they can connect to—which often leaves out a large portion of your environment.
That’s why Zero Trust starts not with access control, but with visibility—knowing what exists before you can protect it.
To build that visibility, you need to identify your Protect Surface—the specific data, applications, assets, and services (DAAS) that matter most. These elements are the foundation of any Zero Trust security architecture.
Identity solutions offer a powerful lens into your environment—but only if applications are integrated. Many aren’t. Legacy systems, modern SaaS apps, and department-owned tools often live outside your secure identity perimeter. These disconnected applications are outside the reach of your identity provider (IdP), so they remain unseen, unmanaged, and unprotected.
These aren’t edge cases. They’re everywhere—and they’re very much part of your attack surface.
Disconnected and non-federated applications create visibility gaps that leave security teams blind. You can’t enforce policy on what you can’t see. You can’t protect what you don’t know exists. And these blind spots are often the root cause of cybersecurity breaches—not because the apps are inherently risky, but because they’re invisible.
As you map your Protect Surfaces, it’s essential to identify the blind spots: applications that aren’t connected to your IAM or IGA tools. A modern identity security solution like Cerby helps close those gaps by integrating any application—no APIs or standard protocols needed—and bringing them under centralized visibility and control, so you can apply consistent Zero Trust principles across your entire ecosystem.
2. Manual security processes are your hidden vulnerability
Manual security processes often start out as necessary workarounds. But over time, they create inconsistency, introduce operational drag, and increase risk. They may work for a handful of users—but not for a modern enterprise.
The bigger issue is what they represent: a culture of hesitancy. When enforcement is too hard or too manual, teams are discouraged from taking proactive steps. Dangers accumulate in silence—not because people aren’t doing their jobs, but because the system makes it too difficult to act. This is how security debt builds up.
Most breaches don’t come from zero-days. They stem from small, preventable breakdowns: a missed user deprovisioning, a weak, reused password, an uncontrolled SaaS tool. And when security is left to end users—expected to rotate credentials, set up MFA, or spot risks on their own—it often doesn’t happen. Not reliably. Not at scale.
Zero Trust security depends on automation. Without it, enforcement becomes optional. And optional enforcement isn’t enforcement at all.
Removing the security burden from end users—and the operational burden from IT—is the only sustainable path to scalable Zero Trust. Eliminating manual tasks removes a major point of failure: human inconsistency. That’s where identity security platforms step in, automating security processes to ensure controls are applied consistently and without friction. The result is stronger security, reduced risk, and an identity foundation built for scale.
3. Security automation and AI aren’t nice-to-haves—they’re the only way forward
One of the most overlooked elements of the Zero Trust security model is step five: monitor and maintain. This is where AI and automation unlock their full potential—not just reducing workload, but actively strengthening your defenses.
AI helps you spot what humans can’t. It surfaces suspicious patterns, flags misconfigurations, and adapts policy based on evolving activity. Automation then acts on those insights, applying guardrails at machine speed. Together, they create a feedback loop that keeps your Zero Trust security strategy dynamic and resilient.
But while defenders debate adoption, attackers have already embraced AI to scale phishing, privilege escalation, and session hijacking. Manual playbooks simply can’t compete with machine-speed threats.
As your environment grows more complex, automation and AI must extend across every layer—including the places traditional tools can’t reach: applications without APIs, identity standards, or centralized control.
4. The best Zero Trust Security Model isn’t a 28-step checklist. It’s five steps done well
Overcomplication kills momentum. I’ve seen vendors turn Zero Trust security principles into an academic exercise—28 steps, dozens of frameworks, and endless diagrams.
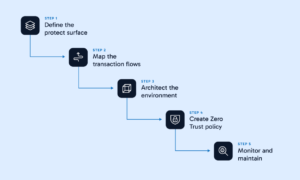
In reality, there are only five steps:
- Define the Protect Surface
- Map the transaction flows
- Architect the environment
- Create your Zero Trust policy
- Monitor and maintain
Start small. Build trust in the process. Zero Trust isn’t about doing everything at once. It’s about starting with what’s in front of you—and extending control, step by step.
Ready to dig deeper?
To see how the modern IAM solutions can help bring every application into your secure Zero Trust environment, please visit Cerby at https://www.cerby.com/.
Zero Trust isn’t new, but it is misunderstood. Unpack what actually drives successful Zero Trust adoption—what works, what doesn’t, and what most organizations are still missing by listening to an on-demand webinar crafted for you. If you’re reassessing your Zero Trust strategy, this is a conversation you don’t want to miss—complete with candid lessons from the field and a framework you can actually use. View the session here!
About the Author: John Kindervag is one of the world’s leading cybersecurity experts and the creator of the Zero Trust Model. With over 25 years of experience as both a practitioner and analyst, he developed the Zero Trust framework while at Forrester Research—redefining modern security strategies. Today, as Chief Evangelist at Illumio, John helps organizations across industries adopt Zero Trust Segmentation. He was a primary author of the U.S. President’s NSTAC Zero Trust report and was named CISO Magazine’s Cybersecurity Person of the Year in 2021.