Webinar
Title: Zero Trust Falls Short Without Network Identity: Lessons from Salt Typhoon
Date: October 1, 2025
Registration: Save your spot here
Abstract
Identity for users, applications, servers, and cloud has matured. Network devices are often the exception. Shared device accounts, SSH key sprawl, limited per-command authorization, and weak session evidence create a gap that attackers exploit. This post explains why traditional tools like Network Access Control do not solve device administration, why telecom and any organization with a physical network face higher exposure, and how to close the gap with identity-aware controls for routers, switches, firewalls, and management planes. Guidance aligns with NIST CSF 2.0 and NIST SP 800-53, plus public advisories on hardening network infrastructure and management interfaces.
Why this gap exists
Network device administration still rides old assumptions. Device CLIs predate modern identity platforms. Shared admin logins and long-lived SSH keys break attribution and enable persistence even when user passwords rotate. Default device logs often miss command intent and sequence, so investigations slow down and audits are painful. The result is a management plane that does not meet today’s identity outcomes in NIST CSF 2.0 PR.AA without deliberate controls and hardening.
NAC is not identity-aware admin control
Network Access Control admits endpoints to the network. It does not govern which human can type which command on a device after admission. Identity-aware authorization for administrators must live on the management plane and at the jump or broker, not only at the port or VLAN. This design aligns with AAA policy tied to an identity provider and with SP 800-53 controls for account management, access enforcement, least privilege, authenticator management, and audit generation.

Port admission is not the same as command authorization.
Telecom reality, broadly applicable
Telecom operators run distributed POPs, multivendor fleets, and strict change windows. Long-lived gear and complex management planes raise identity risk when controls are weak. Similar realities exist for any enterprise with campuses, branches, or factories. Recent public reporting describes state-sponsored activity that targets communications infrastructure and other critical sectors, often with valid-account abuse and living-off-the-land techniques.
Public reporting this summer indicated Salt Typhoon accessed a U.S. National Guard network for many months. Regardless of sector, the lesson is that valid accounts and native tools shorten the attacker path from foothold to impact.
What identity-aware network administration looks like
- Unique admin identities. No shared device accounts. Why it matters: attribution, revocation, and forensics. KPI: percent of device families with unique named admin logins enforced.
- AAA at device logins with RADIUS or TACACS+ tied to an IdP. Why it matters: centralized policy and immediate access revocation. KPI: percent of devices enforcing AAA against the enterprise IdP.
- Per-command allow, deny, or route to approval for risky operations. Why it matters: least privilege at command time, not only at login. KPI: percent of privileged sessions governed by command policies.
- Session capture with integrity and metadata. Why it matters: evidence for investigations and audits. KPI: percent of admin sessions recorded with verified integrity.
- SSH key hygiene. Inventory, age targets, rotation on use, approvals for AAA changes. Why it matters: removes silent persistence. KPI: median key age and percent of keys rotated on schedule.
- Analytics on command streams with alerts into SIEM and SOAR. Why it matters: detect misuse of valid accounts and living-off-the-land activity. KPI: mean time to detect policy violations in command streams.
- Break-glass controls. Why it matters: resilience without bypassing identity. KPI: break-glass sessions at or below 5 percent of admin activity with same-day review.
- High availability for brokers and AAA. Why it matters: identity control must not be a single point of failure. KPI: broker and AAA availability at or above 99.9 percent.
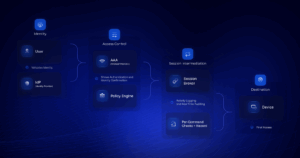
Identity provider and AAA drive policy that the broker enforces per command before a device executes anything, and the broker records the session.
30, 60, 90 day rollout
Day 0 to 30. Foundations and scope.
Owners: Network lead, Identity lead, Security operations.
- Inventory device admin paths, shared accounts, and SSH keys across top vendors.
- Pick two high-impact device families and enforce unique identities via AAA.
- Turn on session recording at jump points or brokers for those families.
- Send session metadata to SIEM and define alert thresholds.
Success metric: at least 60 percent of admin traffic for in-scope devices brokered and recorded.
Risks to watch: change-window collisions, legacy firmware gaps, shadow admin paths.
Rollback test: validate console access plan and automatic rollback for AAA changes.
Day 31 to 60. Expand and harden.
Owners: Same as above, plus audit and compliance.
- Block or require approval for AAA and logging changes.
- Add per-command allow and approval rules for risky operations.
- Set SSH key age targets, remove stale keys, and rotate keys on first use.
Success metric: per-command policies active for 50 percent of privileged sessions on in-scope devices.
Risks to watch: break-glass abuse, incomplete log integrity.
Rollback test: simulate failed broker and confirm HA and fallbacks.
Day 61 to 90. Operationalize.
Owners: SecOps with NetOps and IAM.
- Extend coverage to remaining top device families.
- Tune SIEM alerts for false positives and add SOAR response playbooks.
- Publish an admin standard and RACI for requesting, approving, executing, recording, and verifying changes.
Success metric: 80 percent of device families on AAA with session recording, 70 percent of privileged sessions governed by command policies, and key age SLO met.
Guardrails: break-glass below 5 percent with same-day review; all AAA changes under dual control.
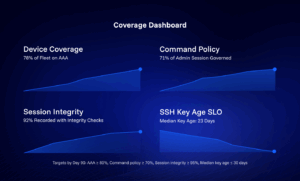
AAA coverage, command-policy coverage, session integrity, and SSH key age SLO with inline sparklines and Day-90 targets.
Compliance mapping quick guide
NIST CSF 2.0 PR.AA
Outcome: identities, credentials, and access are managed by risk.
In practice: unique accounts, AAA to IdP, and least-privilege enforcement at command time.
NIST SP 800-53 AC-2, AC-3, AC-6, AC-17, IA-5, AU-9, AU-12
Outcomes: account management, access enforcement, least privilege, remote access, authenticator management, protection of audit information, and audit generation.
In practice: named admin accounts, role-based policies tied to AAA, key rotation, tamper-evident session storage, and command-time authorization.
NERC CIP-005 and CIP-007
Outcomes: electronic security perimeters and system security management including accounts and logging.
In practice: brokered access across ESP boundaries, central AAA, and recorded sessions for high-value devices.
IEC 62443
Outcomes: identification, authentication, and access control across zones and conduits.
In practice: enforce identity at zone boundaries and on the management plane for industrial and network devices.
CISA guidance on management interfaces and secure-by-design
Outcomes: reduce risk from internet-exposed management interfaces and prioritize built-in security features.
In practice: remove exposure, centralize admin paths, require AAA and logging by default.
Key takeaways
- Most device admin paths still lack identity-aware control.
- Valid credentials and native tools remain the fastest attacker route from foothold to impact.
- Command-time authorization and trustworthy session evidence are the control points that change outcomes.
- Start where blast radius is highest, then expand coverage quickly.
Call to action
Register for the IDSA webinar on October 1, 2025 to go deeper on these topics: https://www.brighttalk.com/webcast/18458/650164?utm_source=IdentityDefinedSecurityAlliance&utm_medium=brighttalk&utm_campaign=650164
Secondary: visit networkpam.com or DM me to set up a short workshop and demo discussion.
Endnotes
- NIST Cybersecurity Framework (CSF) 2.0, PR.AA outcomes. NIST.gov.
- NIST Special Publication 800-53 Rev. 5. AC, IA, AU control families. NIST.gov.
- CISA and partners. Guidance on management interface exposure and hardening network infrastructure. cisa.gov.
- DOJ press release on disruption of PRC-linked botnet used to conceal intrusions against critical infrastructure. justice.gov.
- Public reporting on Salt Typhoon dwell time in a U.S. National Guard network. WIRED and Reuters, July 2025.
About the Author: Craig Riddell is Vice President of Technology and Field CISO, Americas at Kron Technologies. A recognized cybersecurity leader with 15+ years of experience in identity and access management (IAM), privileged access security, and Zero Trust, Craig has helped global enterprises secure critical infrastructure and reduce risk.
He’s a CISSP and Certified Ethical Hacker, known for bridging technical security and business strategy to help organizations strengthen their security posture and drive growth.
About the Company: Kron Network PAM gives you complete control over privileged access to your network—who can log in, what they can do, and how it’s tracked.
Purpose-built for network infrastructure. Simple to deploy. Scales with your environment.








