Webinar
Title: Zero Trust Falls Short Without Network Identity: Lessons from Salt Typhoon
Date: October 1, 2025
Registration: Save your spot here
Abstract
Salt Typhoon highlights how valid credentials and built in tools can turn network administration into an attacker highway. This post walks a likely attack chain in plain language and shows where identity aware device controls would interrupt the sequence without malware signatures or agents. The focus is telecom first, and the same lessons apply to any organization with a physical network footprint.
What Happened, In Plain English
Open source reporting describes a months long intrusion into U.S. networks by a People’s Republic of China linked actor referred to as Salt Typhoon. Access and persistence relied on valid accounts and legitimate management utilities rather than custom malware. Long dwell time becomes more likely when device administration is not tied to a person and when powerful actions are not checked at command time.
Identity Centric Attack Chain and Where To Break It
1. Initial access with a valid admin credential or stolen SSH key.
Break point: require unique admin identities, enforce Authentication, Authorization, and Accounting (AAA), and implement an SSH key lifecycle policy that covers discovery, owner attribution, rotation on use, and age targets.
2. Foothold through legitimate management paths such as SSH or HTTPS.
Break point: use a session broker that binds each device session to a person, captures the session with integrity, and indexes activity for search and review.
3. Lateral movement across devices using remote services.
Break point: apply per command authorization with explicit allow, deny, or require approval. Use time boxed elevation for sensitive changes so standing privilege stays low.
4. Persistence by modifying authorized keys or AAA configuration.
Break point: block AAA and key changes unless they go through an approval workflow. Alert your Security Information and Event Management system (SIEM) on any attempt.
5. Defense evasion by reducing log quality or weakening AAA.
Break point: protect session records with integrity controls, monitor for logging and AAA configuration changes, and escalate alerts to an on call approver when high risk settings are touched.
Why Telecom and Physical Networks Should Care
Public U.S. advisories note that communications infrastructure is a named target. Multi vendor fleets and distributed sites expand the blast radius if one device identity is compromised. The same pattern affects campuses, factories, logistics hubs, and branch heavy enterprises where network devices are administered daily through powerful but legitimate tools.
Practical Safeguards That Do Not Slow Operations
- Identity bound logins at the device through AAA. No shared accounts.
- Per command authorization for high risk operations with approvers reachable on call.
- Time boxed elevation for sensitive tasks so powerful access expires by default.
- Session capture with integrity controls and searchable metadata for accountability.
- SSH key lifecycle policy with discovery, ownership, rotation on use, and age targets.
- Written approvals for AAA and logging changes, with alerts to SIEM on every attempt.
Key Takeaways
- Salt Typhoon illustrates how administration paths can become attack paths when identity is not enforced at command time.
- Command time checks interrupt credential misuse without agents on network devices.
- Harden jump points and management planes first, then expand across device families.
How To Start This Week
1. Turn on session brokerage for SSH and HTTPS logins in one pilot segment.
2. Enforce unique admin identities in AAA for your top two device families.
3. Add per command policies for Tier 1 risky actions and require approvals.
4. Block AAA and logging changes without written authorization and alert to SIEM.
5. Start SSH key discovery and rotation on use, with age targets documented.
Compliance Mapping, At a Glance
| Safeguard | NIST CSF 2.0 | NIST SP 800-53 | NERC CIP (if in scope) | IEC 62443 (if in scope) | Notes |
|---|---|---|---|---|---|
| Unique admin identities via AAA | PR.AA | AC-2, IA-2 | CIP-004, CIP-007 | 3-3 SR 1, SR 2 | No shared accounts |
| Per command authorization with approvals | PR.AA | AC-6, AC-17 | CIP-007, CIP-010 | 3-3 SR 2 | Tie commands to a person |
| Time boxed elevation | PR.AA | AC-6 | CIP-007 | 3-3 SR 2 | Reduce standing privilege |
| Session capture with integrity | DE, PR.PS | AU-12, AU-9 | CIP-007 | 3-3 SR 6 | Searchable, tamper evident |
| SSH key lifecycle policy | PR.AA | IA-5 | CIP-007 | 3-3 SR 1 | Discovery, ownership, rotation |
| Alerts on AAA and logging changes | DE | AU-6, SI-4 | CIP-007, CIP-010 | 3-3 SR 6 | Send to SIEM and reviewers |
Attack Chain Swimlane: Identity Controls Cut The Chain
| Lane | Initial access | Foothold | Lateral movement | Persistence | Exfiltration |
|---|---|---|---|---|---|
| Attacker | Use stolen credential or SSH key | Login via SSH or HTTPS | Pivot to other devices | Modify keys or AAA settings | Exfil configs or data |
| Jump host | Compromised admin PC or jump box | Acts as management conduit to device | Staging point for pivots | Staging for configuration changes | Outbound copy path to external |
| Network device | Device accepts admin login | Legitimate commands execute | Trusts remote sessions | AAA or keys changed | Data leaves device perimeter |
| Security controls (break points) | Unique admin identities via AAA. No shared accounts. SSH key discovery and owner attribution | Session broker binds the session to a person. Record with integrity and index for search | Per command authorization. Allow, deny, or require approval for risky actions. Time boxed elevation for sensitive tasks | Block AAA and key changes without approval. Alert SIEM on any attempt | Integrity protected session logs. Alert SIEM on AAA or logging changes |
Attack stages on network devices with identity controls interrupting each step.
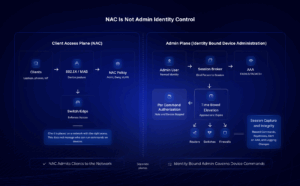
NAC admits clients to the network. Identity bound administration governs who can run which commands on network devices.

Join the vendor neutral discussion on how to bring identity to the network layer.
Webinar: Zero Trust Falls Short Without Network Identity: Lessons from Salt Typhoon
When: October 1, 2025. Time: 11:00 AM, U.S. Central Time (CT) – Available on demand after October 1.
Registration: Save your spot here
About the Author: Craig Riddell is Vice President of Technology and Field CISO, Americas at Kron Technologies. A recognized cybersecurity leader with 15+ years of experience in identity and access management (IAM), privileged access security, and Zero Trust, Craig has helped global enterprises secure critical infrastructure and reduce risk.
He’s a CISSP and Certified Ethical Hacker, known for bridging technical security and business strategy to help organizations strengthen their security posture and drive growth.
About the Company: Kron Network PAM gives you complete control over privileged access to your network—who can log in, what they can do, and how it’s tracked.
Purpose-built for network infrastructure. Simple to deploy. Scales with your environment.








